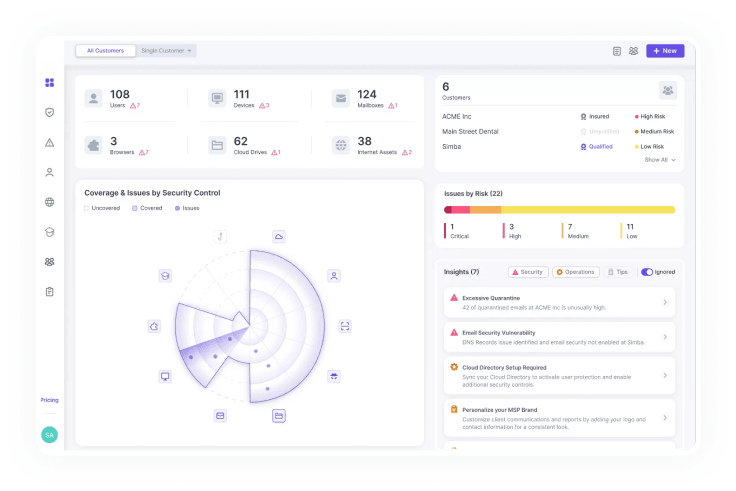
Enterprise-grade security
Level up your cybersecurity game with Beacon
Experience the power of a consolidated solution that reduces costs and helps stop the cyber breaches.
Access our Cybersecurity expertise without breaking the bank
- Are you a sole trader or business with up to 250 employees?
- Have your customers received e-mails impersonating your business recently?
- Are you aware of the cyber threats and tactics that are constantly evolving?
- Does your business require protection against these evolving cyber threats?
If you have answered yes to any (or most) of these questions, contact us to ask how we can help you improve your cybersecurity posture that won't cost you an arm and a leg.
B
Baseline Assessment
Refers to the initial assessment or evaluation of an organisation's cybersecurity posture to establish a baseline understanding of its strengths, weaknesses, and areas for improvement.
E
Education and Training
Represents the ongoing education and training initiatives aimed at raising cybersecurity awareness among employees, equipping them with the knowledge and skills necessary to recognise and respond to security threats effectively
A
Advanced Controls Implementation
Signifies the implementation of advanced cybersecurity controls and measures to enhance the organisation's resilience against sophisticated cyber threats.
C
Continuous Monitoring and Improvement
Emphasises the importance of continuous monitoring of cybersecurity metrics, performance indicators, and threat intelligence to proactively identify and address evolving security challenges.
O
Organisational Alignment and Governance
Highlights the need for strong organisational alignment and governance structures to ensure that cybersecurity objectives align with business goals and priorities.
N
Next-Generation Protection
Represents the full adoption of Beacon Pro helps organisations improve their cyber posture and stay ahead of emerging threats in the ever-evolving cyber landscape
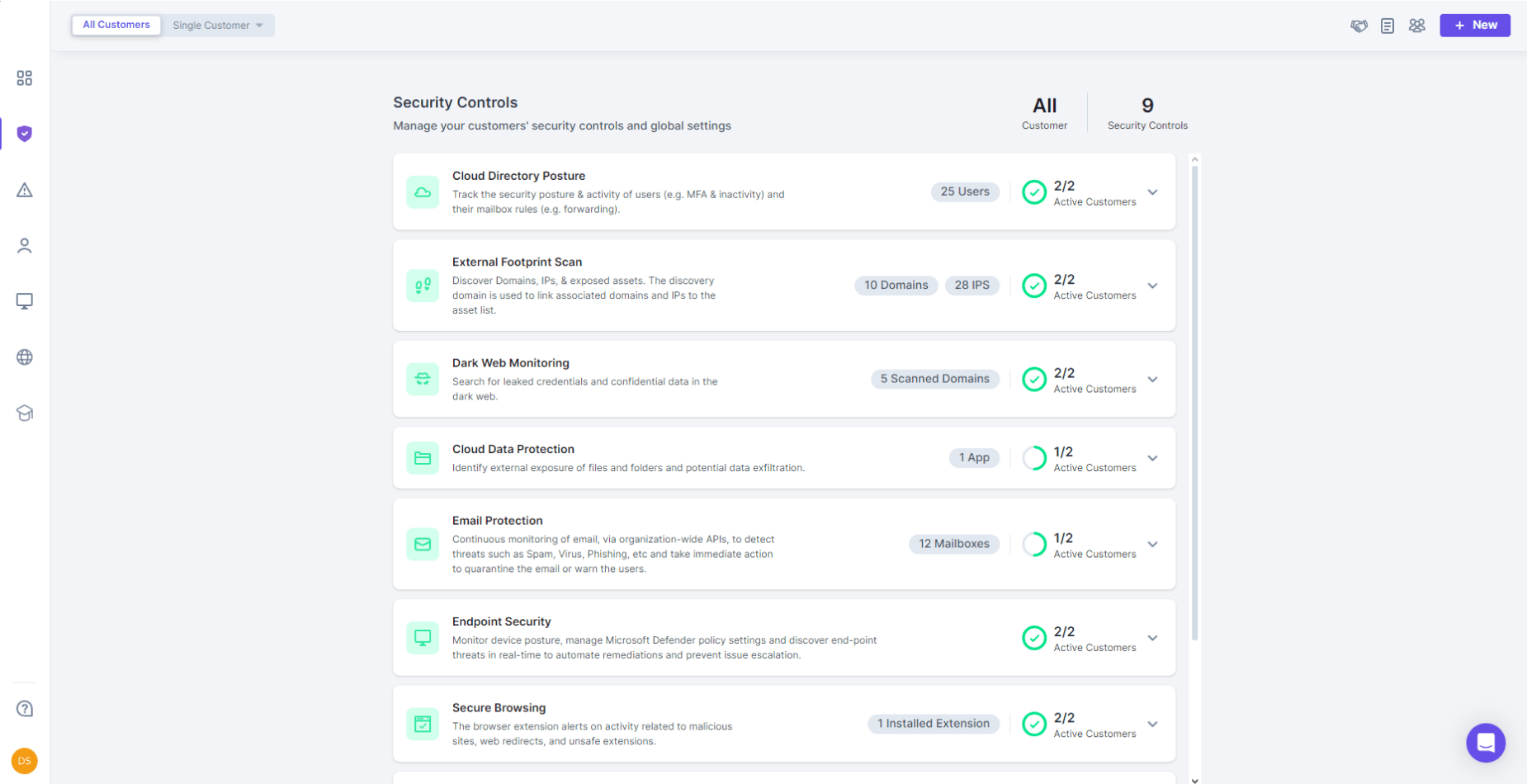
- Active cybersecurity
- Cybersecurity Audits
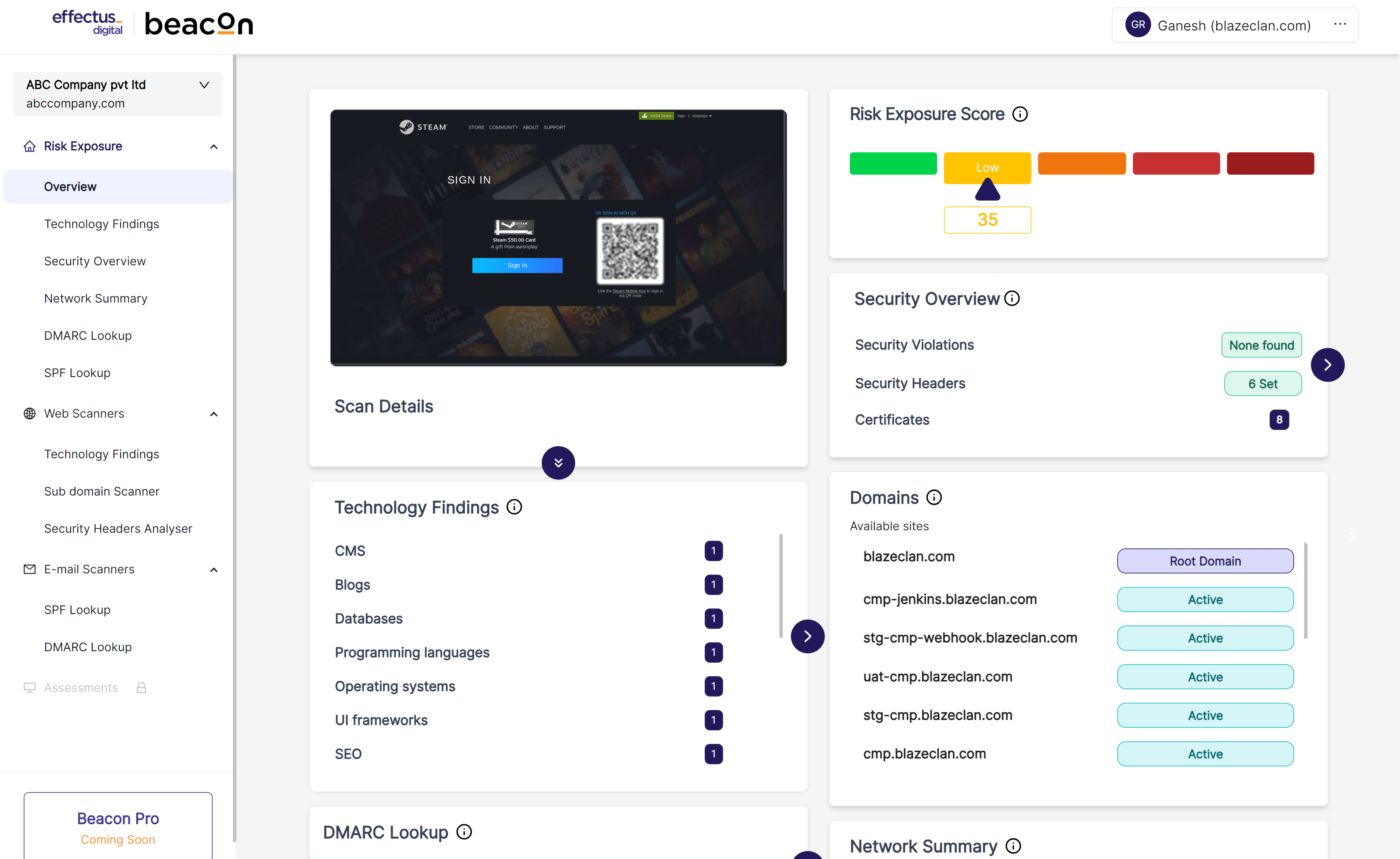
Active cybersecurity
Simplicity at the Core
Experience Comprehensive Cybersecurity
Multilayered cybersecurity platform built for small to medium-sized businesses to protect against Cyber threats.
Email Security
Awareness Training
Secure Browsing
Phishing Simulation
Protect Your Business
From the Inside and the Outside
You can have confidence that your systems will be continuously monitored, and a team of security experts will be readily available 24/7 to defend and manage your organisations digital assets.
External Risk
Gain actionable insights on external threats by scanning digital footprint and exposed vulnerabilities
Email Security
Stay ahead of potential email threats by leveraging a user-friendly active protection
Cloud Data
Enable cloud data protection to achieve a safe and secure data collaboration with external users
Awareness Training
Equip employees to be the first line of defence against the evolving landscape of cyber threats
Endpoint Security
Protect laptops, and desktops from cyber threats such as malware, and ransomware
Secure Browsing
Keep your browser secure with the browser extension for protection against viruses and malicious sites
Phishing Simulation
Continually simulating cyber attacks like phishing emails to highlight weak spots
Insurance
Transfer the cyber risk associated with evolving cyber threats with tailored coverage at the right price
Ready to level-up your cyber posture?
Our Pricing Plans
Get Started for free
- Monthly
- Annually
Free
$0
/month /staff
External Risk Scan
Detailed Scan Report
Check your suppliers and vendors
Cyber Insurance Readiness- Up to 45 mins Consult
Essential
$29
/month /staff*
*Price is per staff (user) email or any email accounts that require monitoring (e.g. [email protected]).
Everything from Free Plan
E-mail security
Cloud Data Protection
Cybersecurity Awareness Training
Endpoint Security
Secure Browsing
Phishing Simulations
Monthly monitoring and alerting
Yearly reviews and progress reporting (for multi year plans)
Premium
$45
/month /staff*
*Price is per staff (user) email or any email accounts that require monitoring (e.g. [email protected]).
Everything from Essential Plan
Quarterly reviews and progress reporting
Weekly monitoring and alerting
Cyber Insurance Readiness
Access to our qualified cybersecurity and governance professionals
Regulatory compliance for your industry / sector
Business Continuity Planning (BCP) planning
Business 360
It is likely, you are already paying for multiple security solutions, products and extensions that are sporadic, unmonitored and may also be costing you a lot more than Beacon. Beacon is designed for small to mid-sized business, packed with big features and is backed by qualified cybersecurity professionals. Our business 360 plan also comes with insurance – making a full 360-degree protection for your business.
Prices discussed via consultations
Features
External Risk Scan
Detailed Scan Reports
Check your suppliers and vendors assets
E-mail security
Cloud Data Protection
Cybersecurity Awareness Training
Endpoint Security
Secure Browsing
Phishing Simulations
Weekly reviews and progress reporting
Daily monitoring and alerting
Access to our qualified cybersecurity and governance professionals
Cyber insurance coverage making it a full 360 protection
Regulatory compliance for your industry / sector
Business Continuity Planning (BCP) planning
Post incident support
Feature List | Free | Essential | Premium | Business 360 |
|---|---|---|---|---|
External Risk Scan Gain actionable insights on external threats by scanning digital footprint and exposed vulnerabilities More info. Access your Cyber Risk Dashboard based on the domain scan that includes the following: - Web technologies findings - Security findings - DMARC lookup i.e., Domain-based Message Authentication, Reporting, and Conformance - SPF lookup i.e., the Sender Policy Framework (SPF), which is an email authentication protocol designed to prevent email spoofing, a common technique used in phishing attacks and email spam. | ||||
Detailed Scan Report Detailed report that is available between 3 to 72 hours including any Dark Web Findings and digital Assets at risk | ||||
Check your suppliers and vendors Understand 3rd party risk by adding domains/assets of your suppliers and vendors | Up to 3 | Up to 10 | Up to 25 | Unlimited |
E-mail security Stay ahead of potential email threats by leveraging a user-friendly active protection | ||||
Cloud Data Protection Enable cloud data protection to achieve a safe and secure data collaboration with external users More info. Protection for Sharepoint Online, Dropbox Teams, Google Workplace, Monday.com and Slack. | ||||
Cybersecurity Awareness Training Equip employees to be the first line of defence against the evolving landscape of cyber threats | ||||
Endpoint Security Protect laptops, and desktops from cyber threats such as malware, and ransomware | ||||
Secure Browsing Keep your browser secure with the Beacon extension for protection against viruses and malicious sites | ||||
Phishing Simulations Continually simulating cyberattacks like phishing emails to highlight weak spots | ||||
Regular reviews and progress reporting Review of your security posture by cybersecurity experts to evaluate progress and guidance on next logical steps | Yearly | Quarterly | Monthly | |
Regular monitoring and alerting We will alert you in case of any suspicious logins, out of date antivirus, unpatched PCs, or laptops etc., and recommend the steps to resolve issues | Monthly | Weekly | Daily | |
Pay per use $255 per hour | Pay per use $180 per hour | Includes 2 Hrs per month Additional at $180 per hour | Includes 4 Hrs per month Additional at $180 per hour | |
1800 E CYBER Get access to Cybersecurity professionals on 1800 E CYBER to guide your cyber maturity | Add on | Add on | ||
Cybersecurity and ICT policies Assistance with uplifting Organisational Policies & Procedures | Add on | |||
Regulatory compliance for your industry / sector Assistance with Regulatory Compliance for your industry (Privacy Act, Notifiable Data Breaches (NDB), Essential Eight, etc.) | Add on | |||
Business Continuity Planning (BCP) planning Assistance with Business Continuity / Disaster Recovery Planning from senior cybersecurity professionals | Add on | |||
Post incident support Full-scale Incident Response and Incident Management assistance with recovery efforts to get you back to business-as-usual | Add on | Add on | ||
Cyber Insurance Readiness Consult From looking at the cybersecurity posture and minimum insurance requirements to assisting you with filling out the form with correct information | Up to 45 minutes | Up to 45 minutes | ||
Cyber Insurance Transfer the cyber risk associated with evolving cyber threats with tailored coverage at the right price | Add on | Add on | Add on |
Don't leave it to chance
What's included in our Audits?
We are experienced in conducting in-depth assessments of cybersecurity controls and presenting the findings to the board and c-suite executives.
NIST 2.0
The NIST Cybersecurity Framework (CSF) 2.0 is the latest framework published by United States Department of Commerce that provides guidance to industry, government agencies, and organisations to manage cybersecurity risks. Our experienced consultants conduct a comprehensive Cyber Risk assessment of the following areas:
Our experienced consultants conduct a comprehensive Cyber Risk assessment of the following areas:
Govern
Detect
Protect
Respond
Recover
ACSC Essential Eight
Australian Cyber Security Centre (ACSC) recommends this base-level assessment that is rated from 0 to 3 to get started on your cybersecurity maturity journey. We help you assess your cyber risk for the following eight controls:
Application Patching
Operating Systems Patching
Multi-factor Authentication
Administrative privileges
Application control
Microsoft Office macros
User Application Hardening
Regular backups
We Are Here To Help You
Frequently Asked Questions
We help startups and small to medium-sized businesses.
Beacon is an integrated and multilayered cybersecurity platform built for small to medium-sized businesses to protect against ever evolving Cyber threats. It is best suited for businesses who do not have dedicated ICT or cybersecurity staff.
Small to medium sized businesses are frequent targets of cybercriminals due to their weaker cybersecurity defences. Common attacks include phishing, ransomware, malware, and insider threats, which can result in financial losses and reputational damage.
Beacon Pro version seamlessly provides continuous monitoring of both internal and external vulnerabilities. In the event of a potential threat, you will be immediately alerted and provided with a remediation plan.
Beacon is designed with business owners in mind that highlights potential risks across your digital footprints. It also has a Return on Investment (ROI) report, illustrating the potential financial impact of a cyber-attack and employee exposure and compares your cyber score with the industry benchmark.